Sep 18, 2023
Did we gain unauthorized access? DEF CON Security shut down the village we were in!
There is no event on the computer hacker calendar as iconic as DEF CON. Born from a party and a challenge issued by the original founder, DEF CON has grown to become a pivotal meeting place for everyone interested in hacking and cybersecurity.
DEF CON 31, held on September 18, 2023, was another stunning example of the diversity and innovation that exists in hacker culture. From ethical hackers to computer programmers and security professionals interested in computer security and computer systems, DEF CON is the perfect place to showcase home computer hacking subculture.

Exploring Technical Weakness to Gain Access: Whether You're in the Hacker Community or Just a Computer Hobbyist
At DEF CON 31, Allthenticate, our humble little cutting-edge cybersecurity company, set up shop in the Physical Security Village, one of many specialized areas catering to specific interests within the broader security field.
We conducted an eye-opening workshop at the security conference on cloning and duplicating MIFARE Classic cards and key fobs using portable Flipper Zeros and other RFID writing tools.
More than 100 malicious hackers managed to break into a maximum-security facility within just five minutes, highlighting severe flaws in standard access-control security measures in defiance of hacker ethic.
Note: The maximum-security facility was represented by a cute, unassuming ASCII door for symbolic purposes. Not quite corporate espionage or the business security nightmare of the century, but we know mass media's pejorative use of black hat hackers.
On the last day of DEF CON, right before Chad Spenksy was about to deliver his final talk to the crowded audience, some chaos unfolded. The village was shut down! It turns out you need a license to implant chips into people, much to the chagrin of another guest and his practice.
Bishop Fox Reveals Major OSDP Vulnerabilities at DEF CON: A Deep Dive into Access Control Security Holes
The event also attracted expert speakers, including Dan Petro and David Vargas from Bishop Fox, who presented their findings about the vulnerabilities of the newly created OSDP (Open Supervised Device Protocol).
This protocol was developed to replace the more vulnerable Wiegand protocol typically used in access control systems. However, the researchers discovered several vulnerabilities within the OSDP Secure Channel, revealing that it may not be as secure as initially thought.
Some of the vulnerabilities in question:
The SCBK, or Secure Channel Base Key, is transmitted in plaintext when a new device joins the network.
Devices can advertise as OSDP-compliant even if they do not support Secure Channel encryption.
An attacker can downgrade the Secure Channel from its initial encryption configuration to an unencrypted mode.
The master encryption key is not generated securely by default and can be easily guessed by attackers.
An attacker can exploit the install mode to obtain the encryption key.
Weak keys can be used in OSDP implementations.
There is no secure in-band mechanism for key exchange in OSDP.
In light of these vulnerabilities, organizations are recommended to hold off on deploying OSDP Secure Channel until the issues are fully addressed and instead consider using alternative protocols such as TLS or IPsec. These discoveries underline the importance of events like DEF CON in driving forward the field of cybersecurity.
The vulnerabilities were discovered by researchers who developed a device called Mellon, which could be used to access control systems.
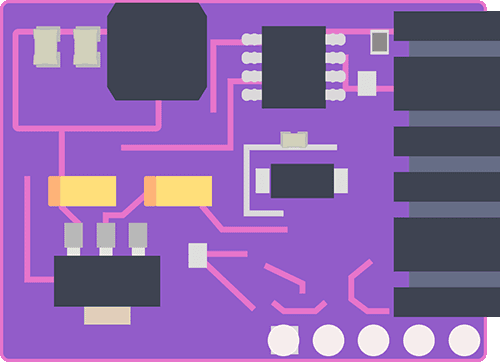
Mellon is a discrete device that can be inserted into the wiring between an access control device and the control panel. With Mellon in place, it can intercept all communications between the devices, including sensitive data such as SCBK.
You can read more in their brilliant blog post breaking it all down.
Introducing Our Next-Gen Access Control Panel: The All-In
In other exciting news, Allthenticate is announcing the upcoming release of our new access-control panel, the ALL IN. After the technical weaknesses on full display at this year's DEF CON, you can bet that our access control solution will be a cutting-edge piece of technology.
Embrace the Future with Allthenticate’s Passwordless, Mobile-Based Authentication
In the vibrant atmosphere of DEF CON, where the world’s brightest minds in cyber security converge to discuss vulnerabilities and cutting-edge solutions, Allthenticate stands out with a keen awareness and deep involvement. At this gathering, where programmer subculture and exceptional computer programming skills are the norms, our team delves into the latest trends in cyber attacks and information security.
Our participation in DEF CON is more than just about staying abreast of developments; it's about actively engaging in the hacker culture that shapes the future of private and corporate computer systems security.
Allthenticate’s pioneering solution is a testament to this commitment. We’ve stepped away from conventional methods to redefine access to computer systems and data. Our passwordless, mobile-based authentication system is not just a response to the challenges discussed by ethical hackers at DEF CON; it’s a proactive step towards a more secure future.
By leveraging advanced technology, we address the vulnerabilities inherent in traditional password-based systems. Our approach involves turning your smartphone into a dynamic key, making access to applications and systems as simple as a swipe on your screen.
In a world where cyber attacks are increasingly sophisticated, targeting both computer hardware and software, Allthenticate’s solution offers a shield of protection. It’s designed with an understanding that information security is not just about erecting barriers but also about creating seamless, user-friendly experiences.
Our participation in events like DEF CON allows us to gather intelligence, conduct penetration tests, and continuously refine our offerings. We are not just one example in the realm of cyber security; we aim to set a new standard, offering comprehensive solutions that resonate with the needs of both the public and the private sector.
This isn't just about making life easier for our users; it's about propelling them into a future where their security is effortless, intuitive, and unobtrusive. At Allthenticate, we are committed to staying at the forefront of cyber security, constantly evolving to meet and exceed the challenges presented in dynamic environments like DEF CON.
Gearing up for DEF CON & Las Vegas: What to expect
DEF CON 31 took place in the heart of Las Vegas, a location as thrilling and dynamic as the event itself. When visiting Las Vegas for DEF CON, or any other event, it's essential to prepare adequately. Comfortable walking shoes are a must for navigating the often busy Vegas Strip, and August temperatures can reach sweltering highs, so be sure to wear light, breathable clothing.
When you've unplugged from the high-energy atmosphere of cybersecurity conferences like DEF CON, the Vegas Strip and surrounding area offer a plethora of gastronomic adventures and exhilarating activities for computer security enthusiast, ethical hackers and malicious hackesr alike. The city's culinary landscape is as diverse as a well-constructed codebase, boasting everything from Michelin-starred restaurants like Joël Robuchon, to the vibrant, bustling street food stalls.
For a taste of Vegas nightlife, head to the iconic Bellagio Fountains and soak up the mesmerizing water and light show. You can look, but you can't swim so don't try and gain unauthorized access. If you're looking for something a little more off-beat, Downtown Las Vegas offers a glimpse into the city's past with its neon museum and vintage casinos.
Computer System Paradise: Capturing the Flags and Digital Delights of Las Vegas for the Tech Enthusiast
The gambling industry and the world of computing have become inexorably intertwined in a modern dance of technology and resilience. Casinos, once solely the realm of intricate mechanical devices and human skill, now primarily rely on advanced computer systems to operate their slot machines, roulette games, and security systems.
This merger of chips and chips, tokens and token rings, is not just a testament to the adaptability of these establishments, but also a commitment to a future where technology and entertainment intersect in seamless harmony. From implementing facial recognition for security to using data analysis for enhancing customer experience, the casino industry exemplifies an intriguing intersection of technology and entertainment that is as vibrant and dynamic as the neon lights illuminating the Las Vegas Strip.
Depending on your outlook, the rush and excitement of the strip can serve to complement the thrill of pioneering cybersecurity developments, making your trip to DEF CON as enriching outside the conference as it is within. Alternatively, if you're longing for Vegas of the past or hate crowds of people, it might be a little overwhelming, so be prepared regardless. Don't share or forget your credit card details.
Tracing the Digital Footprints: The Evolution of Computer Hacking from its Inception to the Present Era
The history of hacking is a riveting saga that parallels the evolution of technology, moving from the shadows of the underground to the limelight of mainstream culture. Its emergence can be traced back to the 1960s, when 'hack' was a term associated with innovative problem-solving among the tech enthusiasts at MIT. It was a time when the pursuit of knowledge and the thrill of exploration drove individuals to push the boundaries of emerging computer systems.
In the 1980s, the narrative around hacking took a darker turn as personal computers started to become common. Cyber explorers (ethical hackers) were replaced by cybercriminals, exploiting technological advancements for personal gain. While the media often portrayed hackers as a menace, this era also saw the formation of hacking groups like the Chaos Computer Club and Legion of Doom, who challenged this notion. Driven by a thirst for knowledge and a desire to expose system vulnerabilities, these groups helped shape the modern definition of ethical hacking and hacker subculture as a whole.
Hacker culture is not just cyber terrorism obsessed masked stock image models breaking into private computer systems, but curious people fascinated with computer code, writing software, with a hobbyists focus.
Fast forward to the new millennium, hacking has evolved into a double-edged sword. On one side lies the threat of cybercrime, with hackers leveraging sophisticated techniques to exploit vulnerabilities and gain unauthorized access in increasingly complex digital systems. On the other side, however, is a growing community of ethical hackers, often referred to as 'white hat' hackers, who use their skills to help secure these systems.
Films, television, and literature have played their part in shifting the perception of hacking from a clandestine act to an intriguing, even respectable, profession. Today, hacking has found its place in mainstream culture and industry, with cybersecurity a cornerstone of modern business. DEF CON, with its inclusive culture and focus on innovation, reflects this journey, offering a platform for hackers of all backgrounds to share knowledge and shape the future of technology.
Unearthing Insecurities: A Retrospective on the History of Physical Security Flaws and Research
The investigation into physical security vulnerabilities has a rich and fascinating history, dating back to ancient civilizations. Strongholds of yore, such as castles and fortresses, were meticulously designed to fend off physical attacks, but their weaknesses were also perpetually studied, paving the way for advancements in siege warfare and fortification design.
However, as technology evolved, so did the complexity and the nature of physical security threats and the corresponding research.
The 19th century marked a significant turning point in the field of physical security with the advent of lock-picking. The art of manipulating a lock's components to unlock it without a key, sparked intense research into creating unpickable locks. This period witnessed the birth of the modern tumbler lock and the double-acting pin tumbler lock, considered unpickable at the time.
In the present digital age, physical security research takes an entirely new dimension, dovetailing with cybersecurity. Experts now delve into how physical flaws can compromise digital security. This research brings forward cases such as the 'evil maid' attacks, where a threat actor gains physical access to a device and compromises it.
Our forward-thinking approach at Allthenticate encapsulates this rich history of physical security research. By transforming your smartphone into a dynamic key, we eliminate traditional vulnerabilities associated with physical security.
We strive to empower users to engage with the world in a safer, more secure manner, keeping pace with the ever-evolving landscape of physical and digital threats. In this endeavor, we are shaping our own chapter in the history of security research, constantly pushing technological boundaries to reinforce your security.
Allthenticate Embraces DEF CON: A Love Story Rooted in Innovation and Progress
At Allthenticate, we recognize this dual nature of hacking, harnessing the power of ethical hacking to enhance our cybersecurity offerings. Not only do we learn from the past, but we also actively engage and contribute to the future, making life easier and more secure for our users. Through our participation in must attend events and cybersecurity conferences like DEF CON, we remain at the forefront of cybersecurity's current trends, ready to meet and exceed the challenges of today and tomorrow.
In conclusion, DEF CON remains one of the most critical events around the world for anyone involved or interested in hacking and cybersecurity. It's a rich melting pot of ideas, innovations, and discoveries that can truly change the world. To stay updated on all things Allthenticate, you can get in touch via LinkedIn or email.
