Understanding
Access Control Attacks
Discover the weaknesses in access control systems and find out how to protect yourself
Access control systems are essential for managing who can enter specific areas within a facility. They are critical for ensuring security in environments ranging from corporate offices to government installations.
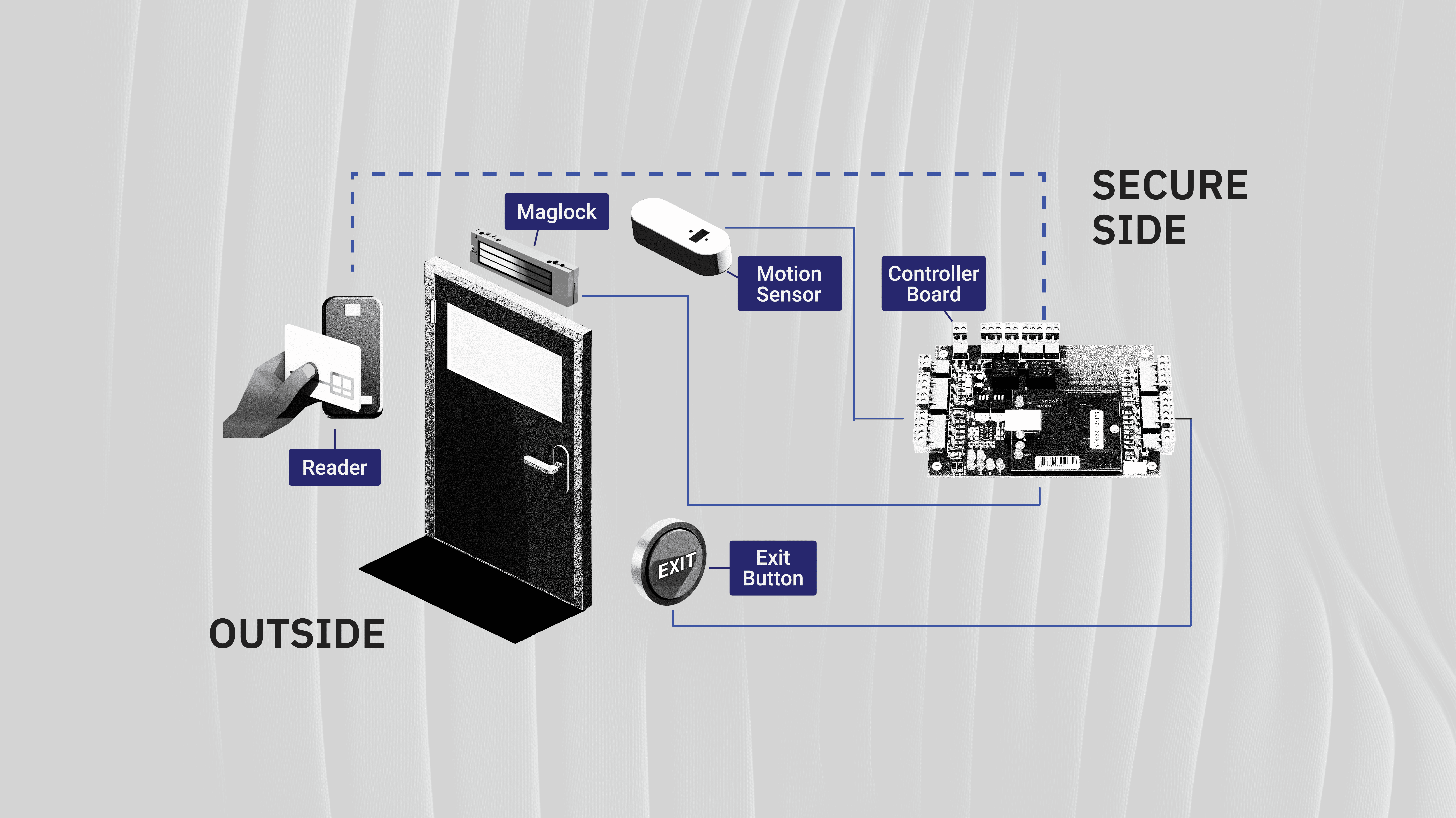
Access control systems are vital for protecting physical spaces - from office doors to server rooms. Traditional systems have vulnerabilities that can be exploited through cloned cards, intercepted signals, or compromised wiring. But more concerning is that these security flaws often go undetected until it's too late.
The fundamental issue: most access control hardware sits exposed on the outside of the door, making it vulnerable to physical tampering and signal interception. Additionally, the complex web of wires connecting readers, sensors and control boards creates multiple potential points of failure.
Understanding
Access Control Attacks
Discover the weaknesses in access control systems and find out how to protect yourself

Access control systems are essential for managing who can enter specific areas within a facility. They are critical for ensuring security in environments ranging from corporate offices to government installations.
Access control systems are vital for protecting physical spaces - from office doors to server rooms. Traditional systems have vulnerabilities that can be exploited through cloned cards, intercepted signals, or compromised wiring. But more concerning is that these security flaws often go undetected until it's too late.
The fundamental issue: most access control hardware sits exposed on the outside of the door, making it vulnerable to physical tampering and signal interception. Additionally, the complex web of wires connecting readers, sensors and control boards creates multiple potential points of failure.
Understanding
Access Control Attacks
Discover the weaknesses in access control systems and find out how to protect yourself

Access control systems are essential for managing who can enter specific areas within a facility. They are critical for ensuring security in environments ranging from corporate offices to government installations.
Access control systems are vital for protecting physical spaces - from office doors to server rooms. Traditional systems have vulnerabilities that can be exploited through cloned cards, intercepted signals, or compromised wiring. But more concerning is that these security flaws often go undetected until it's too late.
The fundamental issue: most access control hardware sits exposed on the outside of the door, making it vulnerable to physical tampering and signal interception. Additionally, the complex web of wires connecting readers, sensors and control boards creates multiple potential points of failure.
Methods
Methods
Methods
Exploit Techniques
Disclaimer: The information provided in this article is for educational and informational purposes only. Allthenticate is committed to enhancing security awareness and readiness in the cybersecurity community. This content is intended to be used responsibly and ethically by security professionals, researchers, and organizations to improve their defensive capabilities.
Disclaimer: The information provided in this article is for educational and informational purposes only. Allthenticate is committed to enhancing security awareness and readiness in the cybersecurity community. This content is intended to be used responsibly and ethically by security professionals, researchers, and organizations to improve their defensive capabilities.
Disclaimer: The information provided in this article is for educational and informational purposes only. Allthenticate is committed to enhancing security awareness and readiness in the cybersecurity community. This content is intended to be used responsibly and ethically by security professionals, researchers, and organizations to improve their defensive capabilities.
Key Components:
Key Components:
External "Readers"
External "Readers"
Reads access credentials from key cards or fobs locally and then relay the read information (typically a number) to the controller
Reads access credentials from key cards or fobs locally and then relay the read information (typically a number) to the controller


Internal "Controllers"
Internal "Controllers"
Receives card numbers and ultimately makes the yes or no decision to trigger the relay, which will unlock the door. These are typically expensive and only support four doors or less
Receives card numbers and ultimately makes the yes or no decision to trigger the relay, which will unlock the door. These are typically expensive and only support four doors or less

Credentials
Credentials
Items used by individuals to verify their identity: just a simple number on legacy systems and cryptographic key on modern systems
Items used by individuals to verify their identity: just a simple number on legacy systems and cryptographic key on modern systems


Cloud Infrastructure
Cloud Infrastructure
Software and servers that manage access data, policies, and logs. Some even permit remote unlocking and locking
Software and servers that manage access data, policies, and logs. Some even permit remote unlocking and locking


Magnetic Lock (Maglock)
Magnetic Lock (Maglock)
A magnetic lock that uses an electromagnet to lock doors hold the door "locked." However, if the power goes out, these are programmed to fail-safe, or "unlocked" for the layperson
A magnetic lock that uses an electromagnet to lock doors hold the door "locked." However, if the power goes out, these are programmed to fail-safe, or "unlocked" for the layperson


Electric Strike
Electric Strike
A solenoid powered strike that will "unlock" when power is applied. Unlock the the maglock, these are fail-secure when the power is off and do not require exit buttons or motion sensors
A solenoid powered strike that will "unlock" when power is applied. Unlock the the maglock, these are fail-secure when the power is off and do not require exit buttons or motion sensors

Exit Button
Exit Button
Because maglocks will hold the door shut when powered, buttons are required on the interior to let people escape in emergencies
Because maglocks will hold the door shut when powered, buttons are required on the interior to let people escape in emergencies



Motion Detector
Motion Detector
Similarly, for maglocks that hold the door locked when powered, motion sensors let people exit the building without much hassle
Motion detectors use infrared, microwave, or ultrasonic waves to detect movement and trigger actions like opening doors or sounding alarms, but can be exploited by actions like vaping, mitigated by additional verification methods and sensor adjustments


Wiegand Protocol
Wiegand Protocol
The most popular communication standard for data transmission between card readers and controllers. It is unencrypted and therefore vulnerable to man-in-the-middle (MitM) attacks
The Wiegand protocol, a widely adopted communication standard for data transmission between card readers and controllers, uses pulses to transmit binary data but is vulnerable to man-in-the-middle attacks due to clear text transmission, which can be mitigated by transitioning to secure protocols like OSDP
The most popular communication standard for data transmission between card readers and controllers. It is unencrypted and therefore vulnerable to man-in-the-middle (MitM) attacks

Open Supervised Device Protocol (OSDP)
Open Supervised Device Protocol (OSDP)
The OSDP protocol was meant to enhance security and interoperability in access control systems through bi-directional communication and encryption
The OSDP protocol enhances security and interoperability in access control systems through bi-directional communication and encryption, allowing secure data exchange and better device monitoring, though it can still be exploited if encryption keys are compromised.





Man-in-the-Middle (MitM)
Wires between the reader and controller are susceptible to physical implants that can steal and replay employee credentials
Exploit tools


Card Cloning
Cards with no or broken encryption schemes can be trivially cloned by walking nearby and employee and wirelessly reading their badge
Exploit tools


Physical Bypass
Mechanical means like using smoke trip the motion sensor, a wire to hit the exit button, or a lockpick can be used to bypass the system entirely. We recommend checking out the courses at Red Team Alliance if you're interested in learning more
Exploit tools
Why Traditional Defenses Fall Short
Why Traditional Defenses Fall Short
Why Traditional Defenses Fall Short
Historically, standard encryption like HTTPS could be bypassed through SSL stripping downgrade attacks. Today, even two-factor authentication can be intercepted by a Web Relay MitM or by leveraging a compromised Certificate Authority. Every HTTPS site is one compromised CA and a DNS attack away from completely broken.
Historically, standard encryption like HTTPS could be bypassed through SSL stripping downgrade attacks. Today, even two-factor authentication can be intercepted by a Web Relay MitM or by leveraging a compromised Certificate Authority. Every HTTPS site is one compromised CA and a DNS attack away from completely broken.
CARD TYPE
CARD TYPE
VULNERABILITY
VULNERABILITY
Tools to Exploit
Tools to Exploit
Weak Encryption
Weak Encryption
Flipper Zero, Proxmark
Flipper Zero, Proxmark
Downgrade
& Relay Attack
Downgrade
& Relay Attack
Weak Encryption
Weak Encryption
Flipper Zero, MFOC, MFUK
Flipper Zero, MFOC, MFUK
Almost All Cards
Almost All Cards
Almost All Cards

Relay Attack
Relay Attack
Proxmark
Proxmark
WIRE PROTOCOL
WIRE PROTOCOL
VULNERABILITY
VULNERABILITY
Tools to Exploit
Tools to Exploit
Better Technology
Better Technology
TECHNOLOGY
TECHNOLOGY
WHY WE LIKE IT
WHY WE LIKE IT
Mifare DESfire EV2 & EV3
Mifare DESfire EV2 & EV3
Resistant to cloning, tampering, and relay attacks
Resistant to cloning, tampering, and relay attacks
PIV Credentials
PIV Credentials
Proper private/public keys; resistant to known attacks
Proper private/public keys; resistant to known attacks
Mobile Credentials
Mobile Credentials
Convenient, secure, can leverage biometrics and PIN on smartphone
Convenient, secure, can leverage biometrics and PIN on smartphone
How Allthenticate Defends Against This
How Allthenticate Defends Against This
How Allthenticate Defends Against This
Allthenticate eliminates the the risk of Access Control Exploits.
Before writing a line of code, we analyzed and actively exploited all of the aforementioned vulnerabilities and specifically designed our patented architecture to be resistant to all of them.
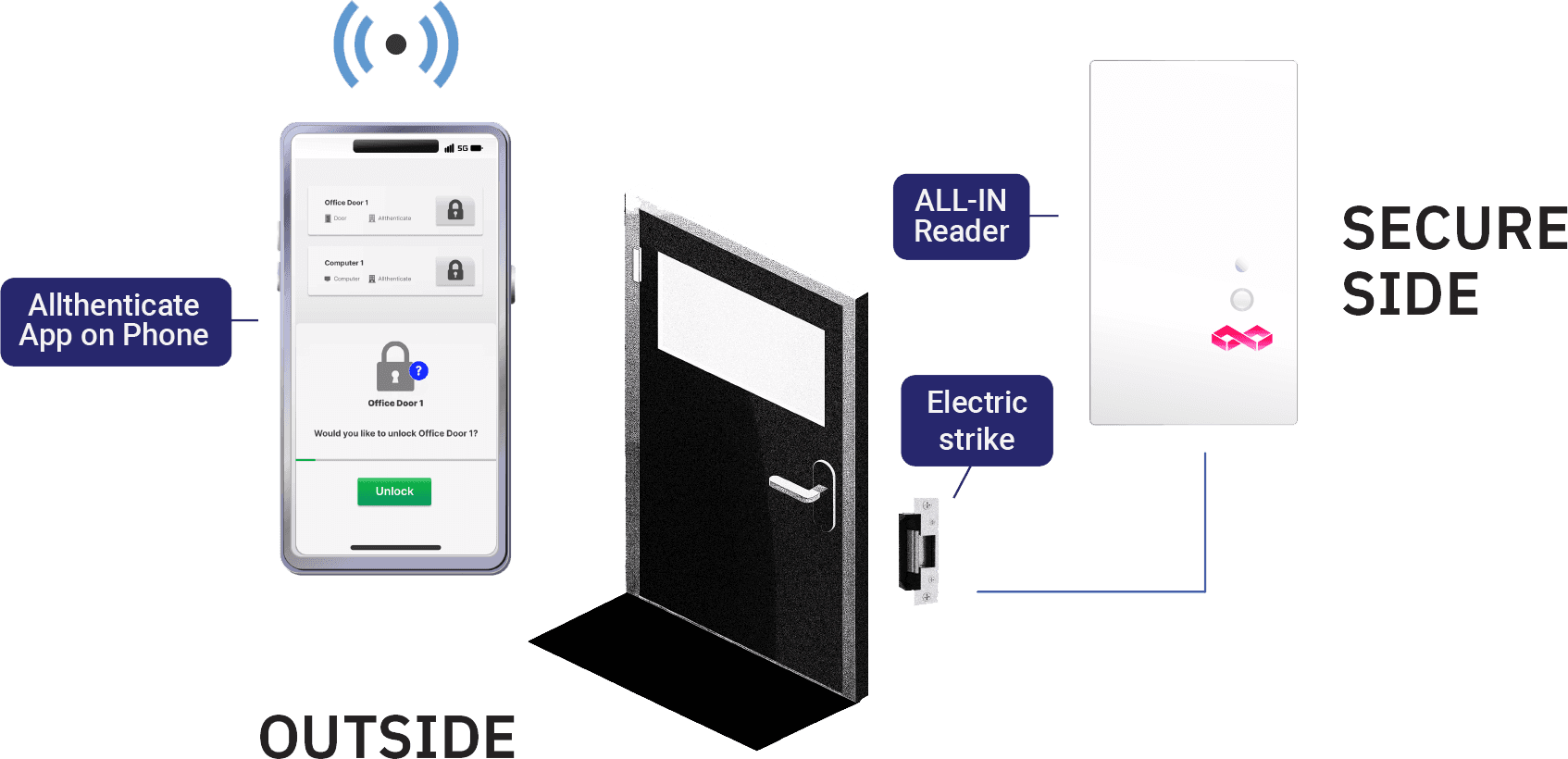


Reader on the inside of the office
Our ALL-IN reader/controller is installed on the secure side of the building as a single unit, leaving no reader or wires exposed to a Man-in-the-Middle (MitM) attack.
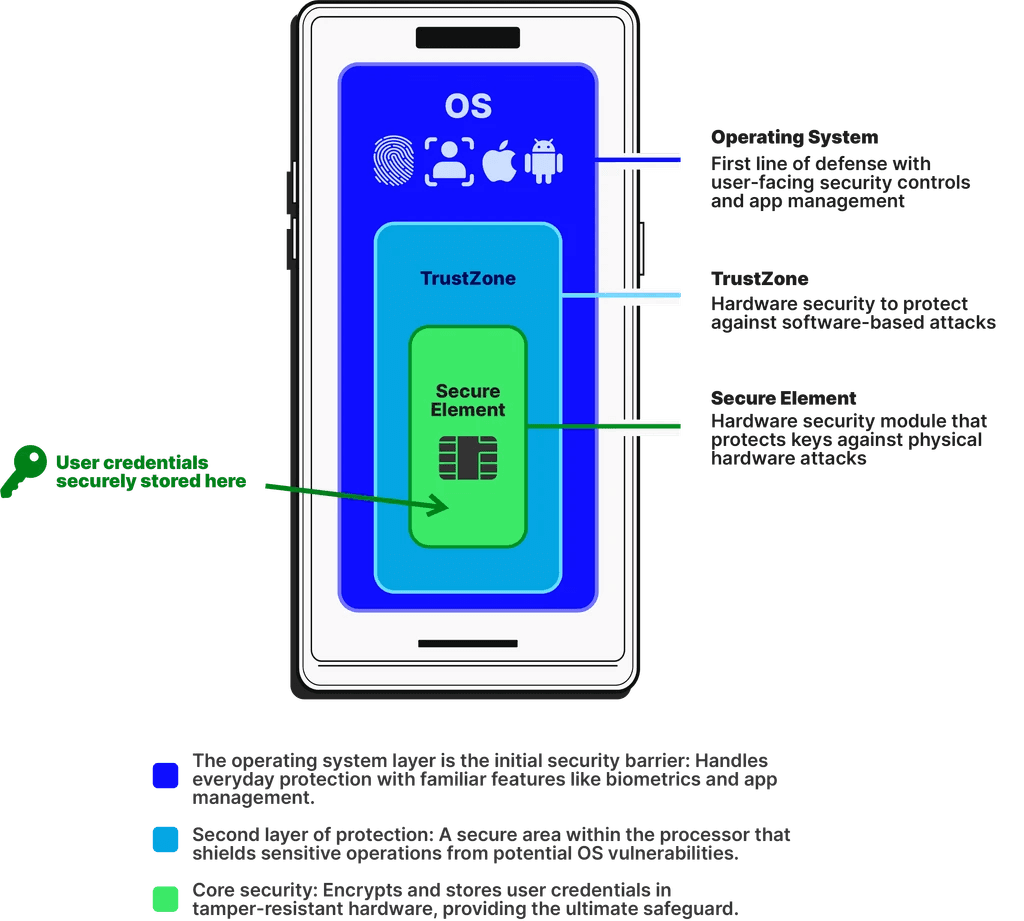


Secure by Design
Your private keys are stored in the Secure Element (SE) on the phone — the same technology in DoD-grade smartcards. Bluetooth connections reduce friction while maintaining best-in-class security. Additionally, TrustZone and biometrics are leveraged to prevent relay attacks, software exploits, physical tampering, and device theft.
Secure your organization by eliminating entire classes of vulnerabilities with Allthenticate.

Secure your organization by eliminating entire classes of vulnerabilities with Allthenticate.
