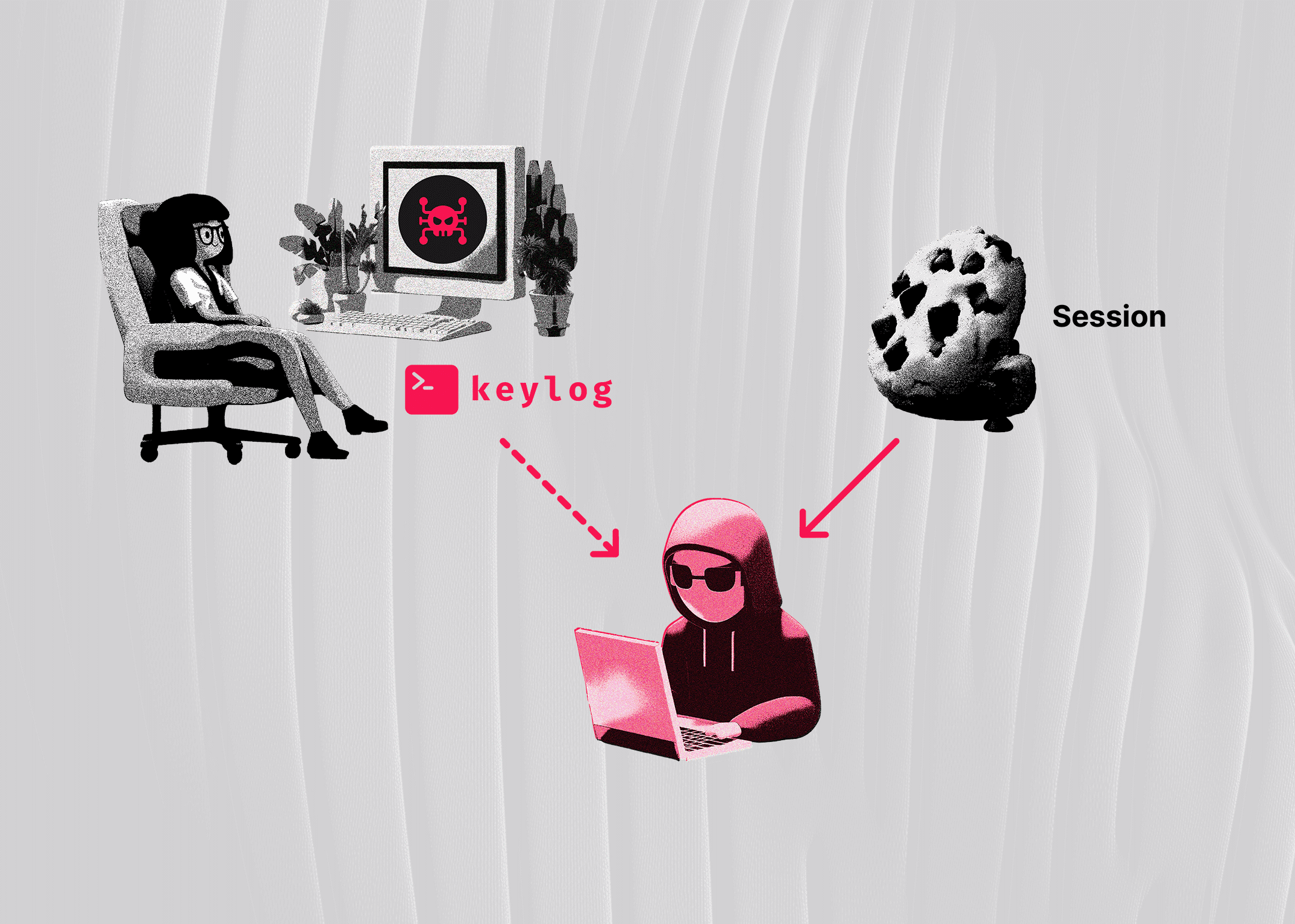
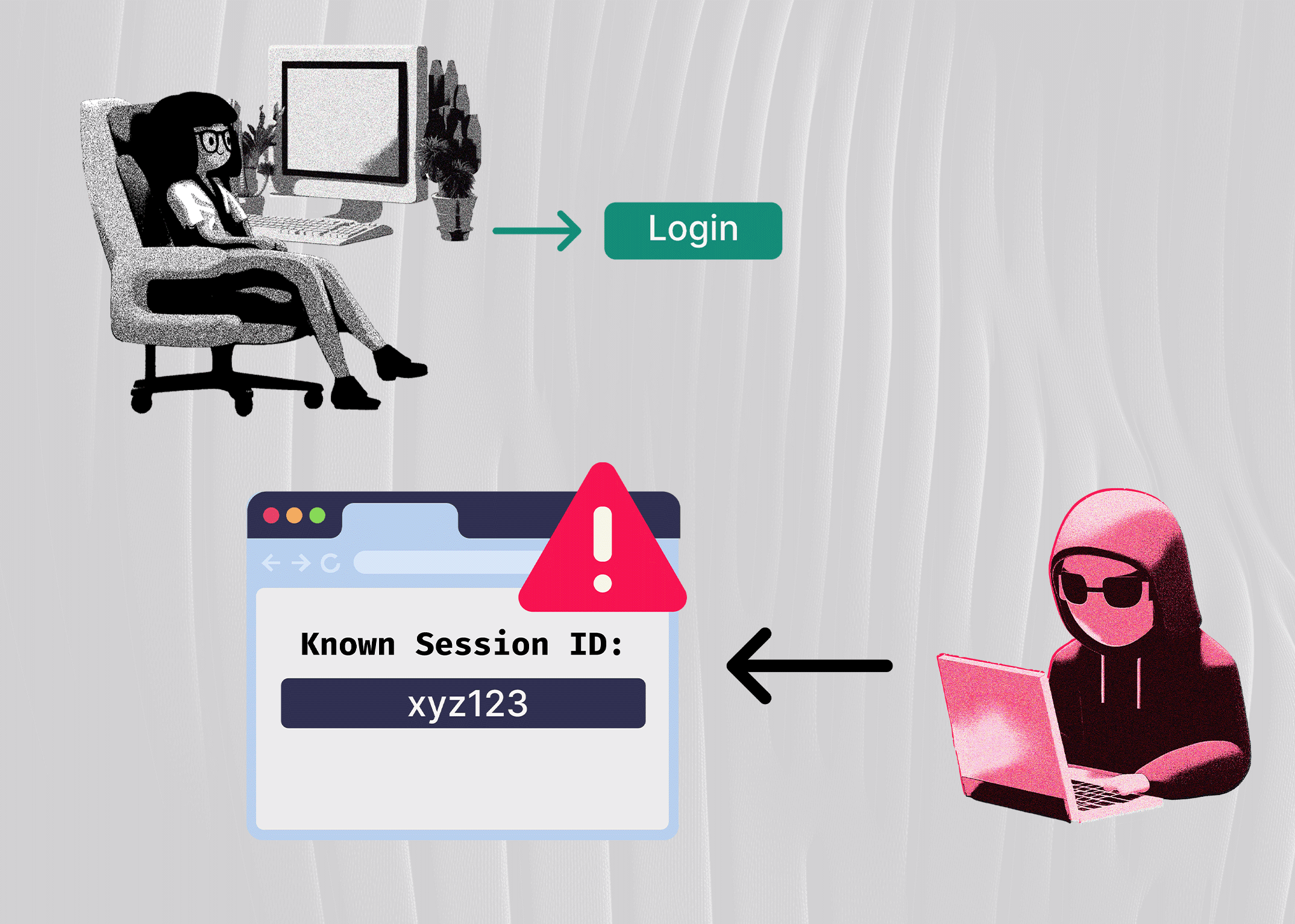
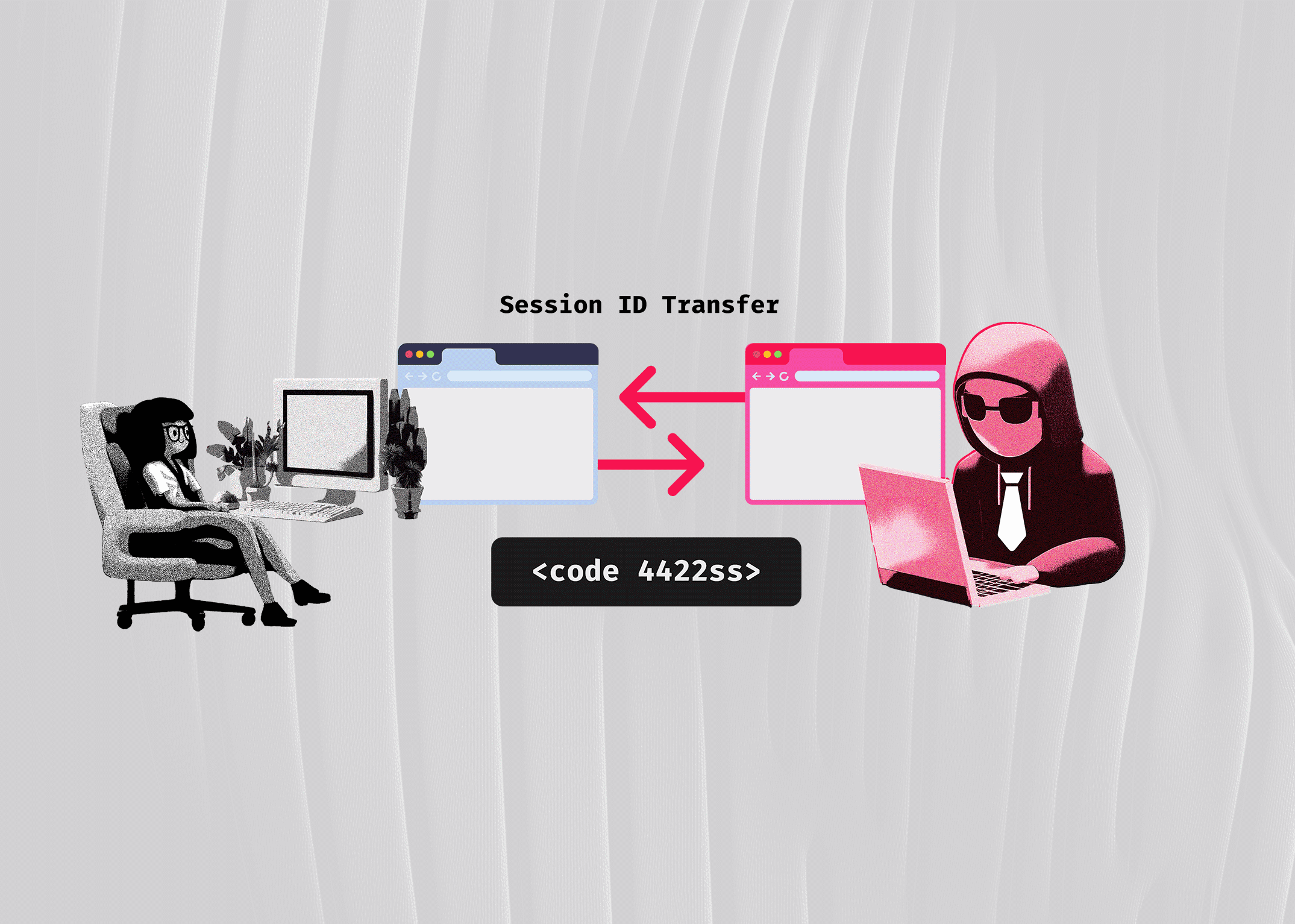
Exploit Techniques
Allthenticate eliminates session hijacking
Since Allthenticate binds your sessions to your phone and uses end-to-end encryption, there is nothing to steal on the network, nothing stored on your computer, and nothing sensitive passed around by your browser.
Simply put: all of the attacks mentioned here are rendered completely ineffective.
Authenticated Actions
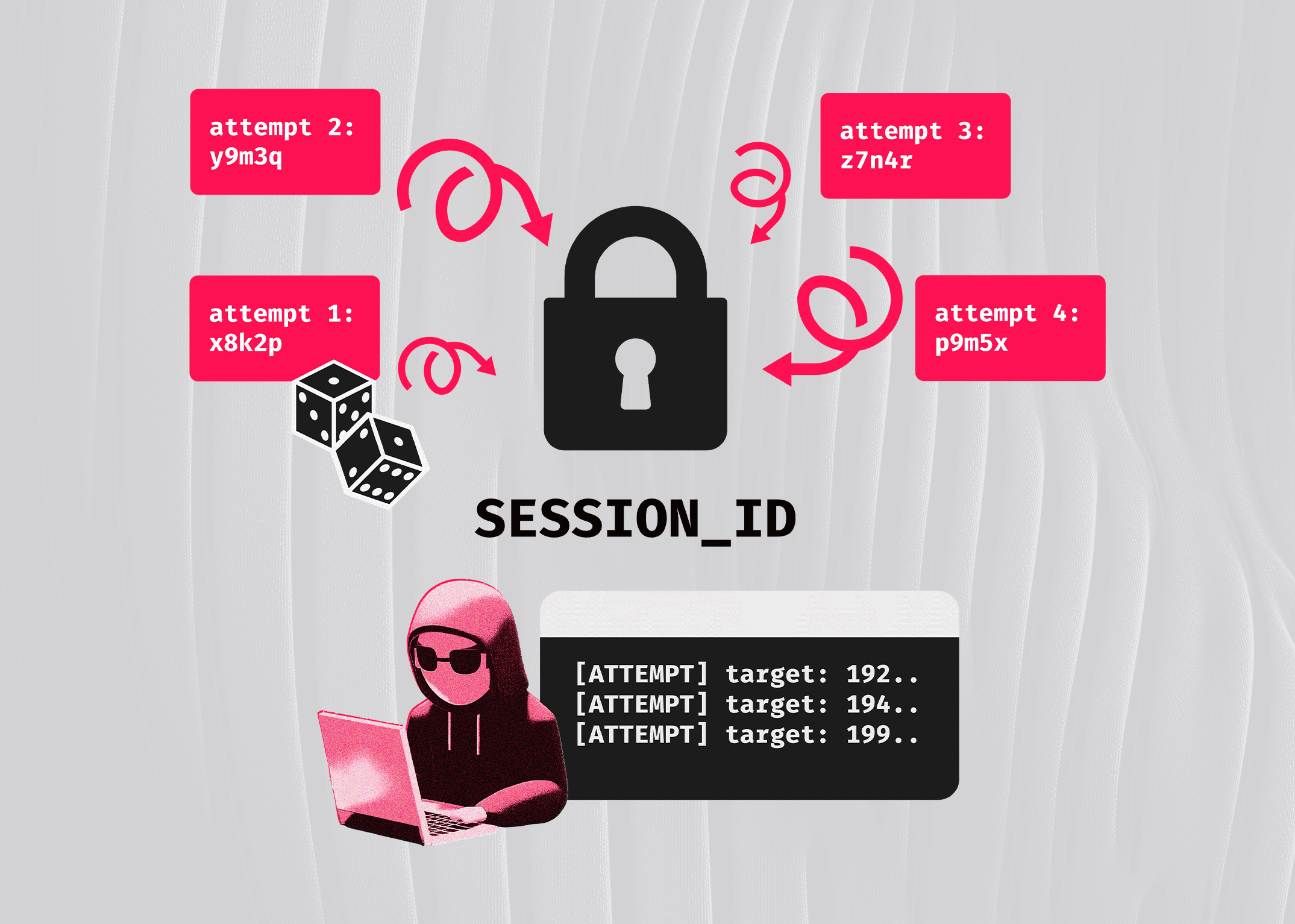
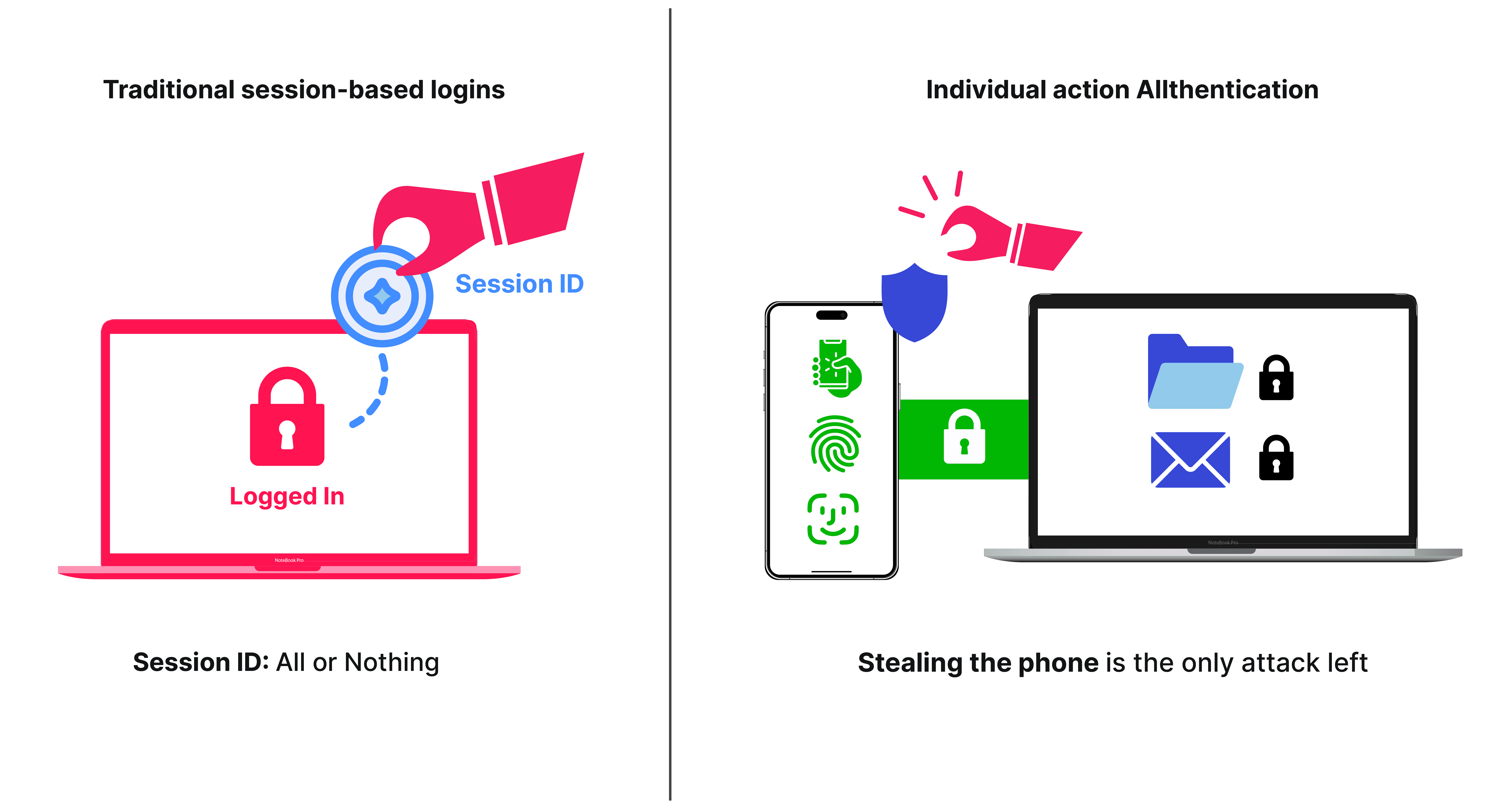
Current session-based login is all or nothing — you are either logged in and can do everything or you are not.
With Allthenticate, every individual action is authenticated, requiring the user's phone to satisfy the request. Therefore, stealing the phone is the only attack left, not a simple cookie value.
To ensure maximum usability, our patented architecture permits three levels of assurance:
Presence: verifies the phone is still nearby
Intent: verifies a human approved the action
Identification: verifies the owner of the account approved the action
Device-Bound Sessions
By binding each action to the secure key stored on the smartphone, Allthenticate ensures that all remote session attacks will be neutered.
The phone is the key. When you walk away, you automatically be "logged out" and everything will magically work again when you return with your phone.