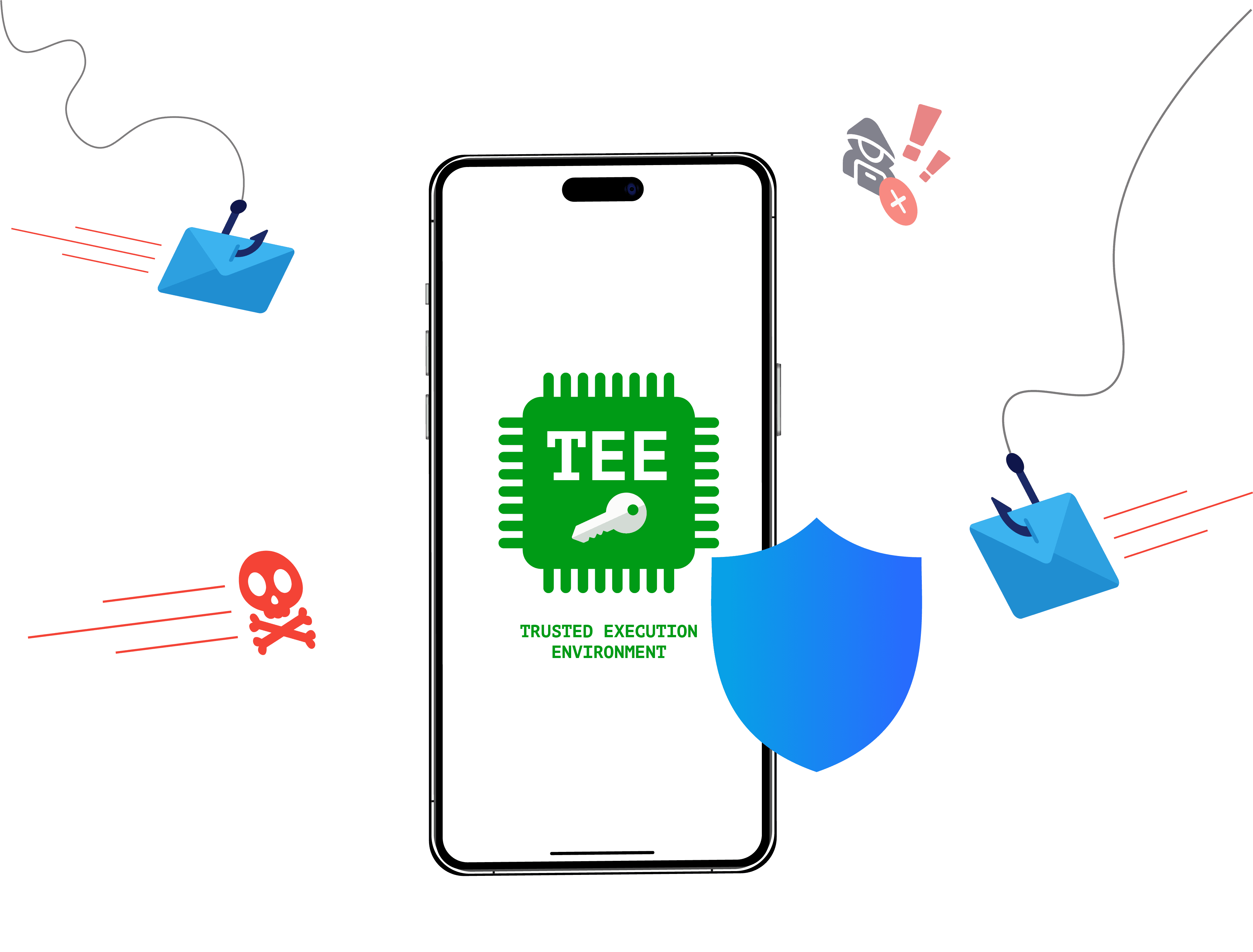
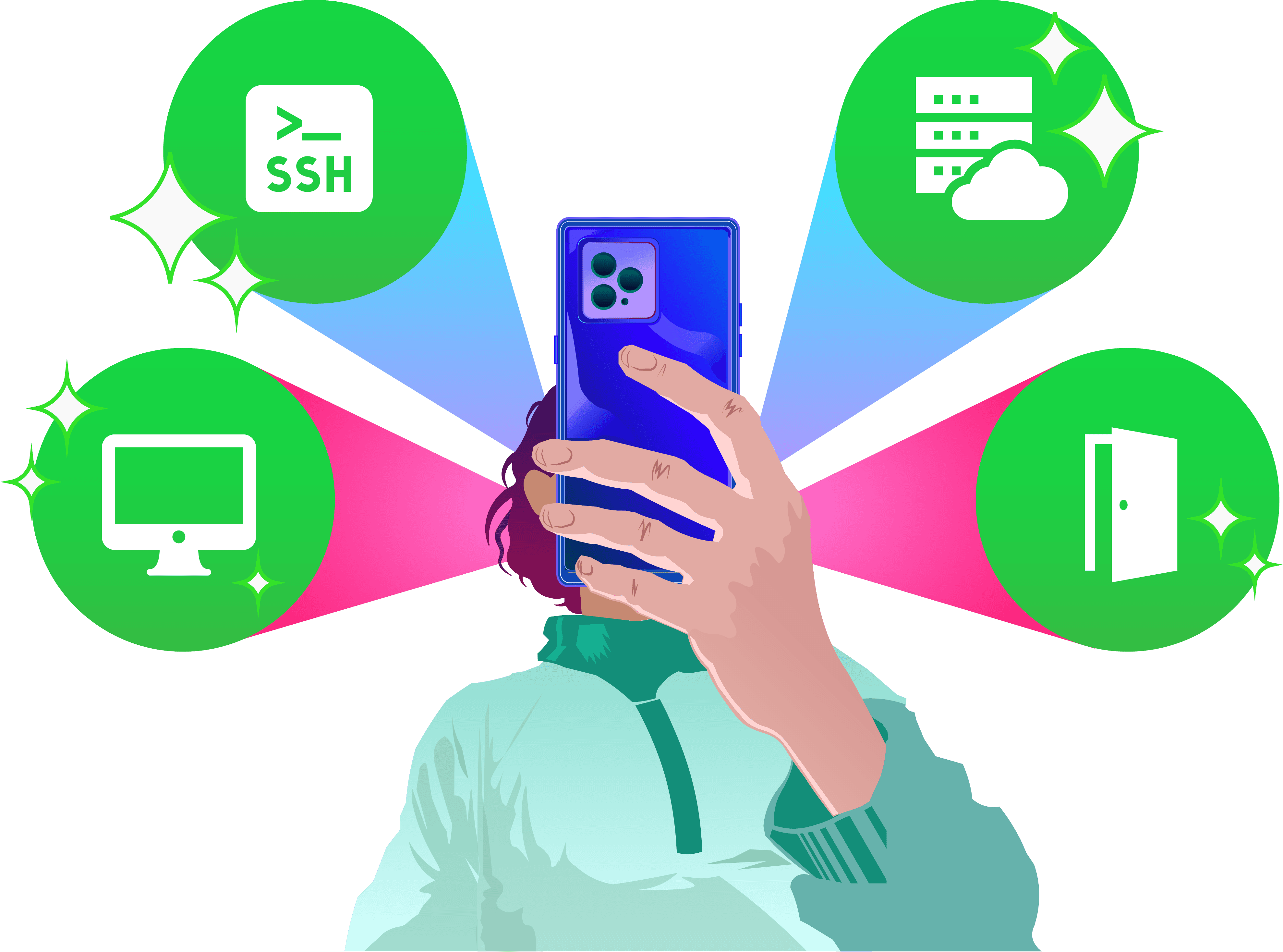
Allthenticate eliminates the primary attack vector for ransomware: credential theft
Only certain users have access to all of the sensitive data that would be targeted by a ransomware attack. Attackers are currently stealing those credentials to login and install their malware. The first step to stopping ransomware is by eliminating their initial ingress vector.
Secure, Phishing-Resistant Credentials
Allthenticate credentials are stored securely in the hardware of your smartphone, making them invulnerable to phishing.
Thanks to a secure, decentralized architecture, they are also secure against man-in-the-middle, MFA fatigue, and session hijacking attacks.
Attackers are going to need to find another way into your systems, because their current vectors are all eliminated.